Throughout their generations, medical records have promised us lowered costs, increased efficiency, and generally better healthcare. However, despite untold dollars and the efforts of some very smart people, we've yet to realize a fully electronic medical record.
Health information technology is far from a new concept. The first EKG machine, used by Alexander Muirhead in 1872, was designed to bring better medical solutions to ailing patients through technology. Today, technology and medicine are almost inseparable. Machines provide comprehensive data throughout the diagnostic path. Magnetic resonance imaging is an excellent example of the type of analysis that could not be completed without very powerful computers.
Yet most of this industry has yet to achieve full electronic sharing of data between patients, primary care physicians, referring physicians, pharmacists, and laboratories.
The Veterans Administration offers a shining example of what's possible. Its EMR systemreaches or exceeds the goals of digital patient record deployment on all levels. That's because the system's data -- each patient's record -- is usable and viewable by everyone within the patient care system. You have truly available data, from the patient's reporting of the chief complaint (at record origination) through the patient's discharge (or record close). All facets of care are encompassed within the same record and the same system.
In the open healthcare market, health information exchanges (HIEs) are supposed to handle this sharing of records across a common data structure. Regional extension centers were supposed to implement HIEs, which are an integral part of the ARRA/HITECH Act. But this plan has failed -- plain and simple. You can spread the blame widely, and many health IT players are doing just that.
Because of HIEs' lack of success, EMR implementations also are threatened, according to a December 2012 California Healthcare Foundation study. "Given the lack of tangible progress in expanding HIE capacity in California through federally funded programs... it is unclear how meaningful the widespread adoption" of electronic health records will be.
When looking at EMR adoption, ARRA/HITECH advocates cite a Medscape study from August (registration required) that found 74 percent of physicians are using these solutions. But there's a lot of disparity among systems, and a lack of leadership should concern IT professionals. According to the Medscape study, 22 percent of physicians said they use Epic systems, but an equal percentage chose the "other" option. Since no single package has a commanding marketshare, there's no common data structure across healthcare providers. Records are not necessarily accessible from system to system, meaning patients will find their information in silos across healthcare providers. Sound familiar?
No Front Runner in EMRs
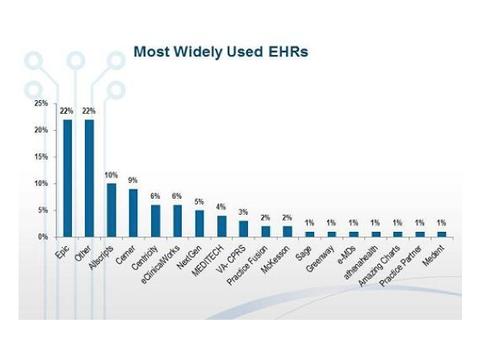
Epic is the leader in the EMR market, an August 2012 report found, but there are many contenders.
(Source: Medscape)
(Source: Medscape)
To realize the promises of procedural efficiencies, reduced costs, and improved care, healthcare itself must recognize something that's true across computing, regardless of industry, type, or size: It has to be easy to share data across platforms. For many generations, documents and spreadsheets have been portable across platforms and between users, irrespective of the relationship between the sharing parties. Any user, from novice to expert, can share media of all types, including videos. However, billions of dollars later, the infrastructure for one set of highly trusted users -- our medical professionals -- is still stymied by this challenge. Healthcare professionals still cannot share digital information between systems.
Frankly, I do not see a cure in the near future. But some sort of exchange medium must be found. We must concoct a common ground for sharing medical data -- for the health of the industry and, more importantly, our citizens.



